Cyber security refers to the practices and procedures a business or individual can implement to reduce the likelihood they fall victim to cyber attacks. Learn more in our blog.
The internet plays a huge role in daily life, from banking and shopping to social media and communication. While it brings convenience, it also comes with risks. Cyber criminals are constantly looking for ways to exploit vulnerabilities, so it's essential to practise good online safety habits.
Our top 23 tips for internet safety
Improving your cyber security can be as simple as reviewing your passwords. Any steps you take will reduce the likelihood that you fall victim to cyber scams, and once you understand what to do it becomes part of your everyday practices.
Review the following tips to make sure you’re doing what you can to stay safe online.
- Keep your email safe and secure
- Install the latest software and app updates
- Turn on 2-step verification (2SV)
- Use a secure password manager
- Back up your most important data
- Create strong passwords (e.g., three random words)
- Review the credibility of every website if you're unsure
- Review all emails before you click links
- Do not post your data publicly
- Do not communicate with people you don't know
- Make your social accounts private
- Avoid using the same password across multiple accounts
- Do not click links from SMS messages if you’re unsure
- Do not respond to unknown accounts
- Do not save your login details on shared devices
- Do not fall for ‘too good to be true’ scams
- Never go through with an action if you’re unsure
- Install antivirus software
- Only download files from trusted sources
- Use a browser that protects you
- Check for common scams using online tools
- Periodically check if you’ve been targeted in a data breach
- Use services that protect your personal information
Tip 1: Keep your email safe and secure
Your email is often used for multiple online services, such as your social media accounts, banking services, government logins, pension accounts and more. If cyber criminals gain access to your email, they can reset passwords, access personal information, and potentially take control of other accounts linked to that email. This makes securing your email one of the most important actions you can take to protect yourself.
Why it’s important
A compromised email account can lead to identity theft, financial fraud, and privacy breaches. Many people use the same password across multiple accounts, which can create a domino effect if one account is hacked. By securing your email with a unique, strong password and using two-factor authentication (2FA), you reduce the risk of other accounts being compromised.
Tips for keeping your email secure
- Create a strong password: Use a combination of uppercase and lowercase letters, numbers, and special characters. Avoid obvious choices like your name, birth date, or other information that is publicly available (such as your partner or pet's name).
- Keep your email password separate: Ensure your email password is not reused across other accounts. This way, even if one account is compromised, your email remains secure.
- Change passwords regularly: Consider updating your passwords periodically to add an extra layer of security, such as every 3-6 months.
- Use two-factor authentication (2FA): Enable 2FA wherever possible. This adds an extra step to log in, such as receiving a code on your phone, and makes it much harder for hackers to access your account.
Tip 2: Keep your devices, apps and software up to date
Keeping your software and apps up to date is one of the simplest yet most effective ways to protect your devices from cyber threats. A device could be your phone, laptop, PC, tablet, TV or any other technology you use. Updates often include essential security patches that fix vulnerabilities in the software. Without these updates, cyber criminals can exploit previous weaknesses to gain access to your device, steal data, or infect it with malware.
Why it’s important
Hackers are constantly looking for vulnerabilities in software, and when they find them, they can use them to launch attacks. Software developers release updates to fix these issues, so if your system or apps are not up to date, you could be leaving your devices exposed. Installing updates ensures that you’re protected against the latest known threats.
Tips for following this practice
- Turn on automatic updates: Enable automatic updates for your operating system, apps, and antivirus software. This way, your devices will always have the latest security patches without needing to manually check for updates.
- Regularly check for updates: Some devices or apps might not update automatically. Make it a habit to check for updates regularly, especially for critical software like web browsers, antivirus programs, and your operating system.
- Update all your devices: Ensure that all devices you use, including smartphones, tablets, and laptops, have the latest updates installed.
Tip 3: Turn on 2-step verification (2SV) for added security
Two-step verification (2SV), also known as 2FA, is an extra layer of security for your online accounts. It requires not only a password but also a second piece of information to log in, such as a code sent to your phone or through a standalone app that generates a code.
Why it’s important
Passwords can be stolen, guessed or leaked, but 2SV adds a second barrier that makes it much harder for hackers to access your accounts. This is especially crucial for accounts that store sensitive information, such as email, banking, and social media. If a hacker tries to log in, they would need both your password and access to your phone or other authentication device, significantly reducing the risk of unauthorised access.
Tips for following this practice
- Enable 2SV on all important accounts: Set up 2SV on accounts that store sensitive data, including email, banking, social media, and online shopping accounts. Many major services, like Google, Facebook, and Microsoft, offer 2SV options.
- Choose the right method: Some services offer multiple ways to set up 2SV, such as SMS codes, authentication apps, or physical security keys. Authentication apps (like Google Authenticator, Authy, or Microsoft Authenticator) are generally more secure than SMS, as SMS codes can sometimes be intercepted.
- Keep backup options handy: When setting up 2SV, most services will allow you to save backup codes. Store these securely in case you lose access and need to recover them.
- Be cautious of phishing: Even with 2SV, be aware that some sophisticated phishing attacks may try to trick you into providing the second factor. Always verify the legitimacy of requests and never share your codes.
Tip 4: Use a secure password manager
A password manager is a tool that helps you create, store, and manage strong, unique passwords for all your online accounts. Instead of trying to remember all of the passwords you use, you only need to remember one master password to access your password manager. This makes it easier to use complex passwords without the need to write them down or reuse the same password across multiple accounts. Password managers offer additional layers of security to access, making them harder to infiltrate.
Why it’s important
Using weak or repeated passwords is one of the biggest security risks online. If a hacker obtains your password from one account, they can easily try it on others, putting all your online activities at risk. Password managers solve this problem by generating strong, random passwords and storing them securely. This not only improves security but also makes logging in more convenient.
Tips for following this practice
- Choose a reputable password manager: Look for password managers with strong encryption and positive reviews. Popular options include LastPass, Dashlane, Bitwarden, and 1Password. Many of these tools also offer features like password auditing and alerts if your passwords are exposed in a data breach.
- Set a strong master password: The master password is the key to your password manager, so make sure it is strong and unique. Avoid using obvious words or phrases, and consider using a combination of characters, numbers, and symbols.
- Enable 2SV for your password manager: Add an extra layer of security by enabling 2SV. This ensures that even if someone tries to access your password manager, they’ll need a second form of authentication to get in.
- Use the password generator feature: Password managers can generate complex, random passwords that are much harder for hackers to guess. Make sure to use this feature when creating new accounts or updating old passwords.
Tip 5: Back up your most important data
Backing up your data involves creating copies of your important files and storing them in a secure location, such as an external hard drive or a cloud-based service. This ensures that if your data is lost, stolen, or corrupted (for example, due to a cyber attack, device failure, or accidental deletion), you have a backup copy that can be easily restored.
Why it’s important
Data loss can happen for various reasons, including ransomware attacks, hardware failures, and natural disasters. Without a backup, losing essential files such as photos, documents, and videos can be permanent. Backing up your data regularly helps protect against these risks, allowing you to recover your files even if something goes wrong.
Tips for following this practice
- Schedule regular backups: Set a schedule to back up your data automatically. Most backup software allows you to set daily, weekly, or monthly backups, ensuring your files are always up to date.
- Encrypt your backups: Protect your backups by encrypting them, especially if you are using cloud storage. This ensures that even if your backup is compromised, your data remains secure.
Test your backups: Periodically test your backups by restoring files to make sure they are working correctly. This helps ensure that your backup process is reliable and that your files can be recovered when needed.
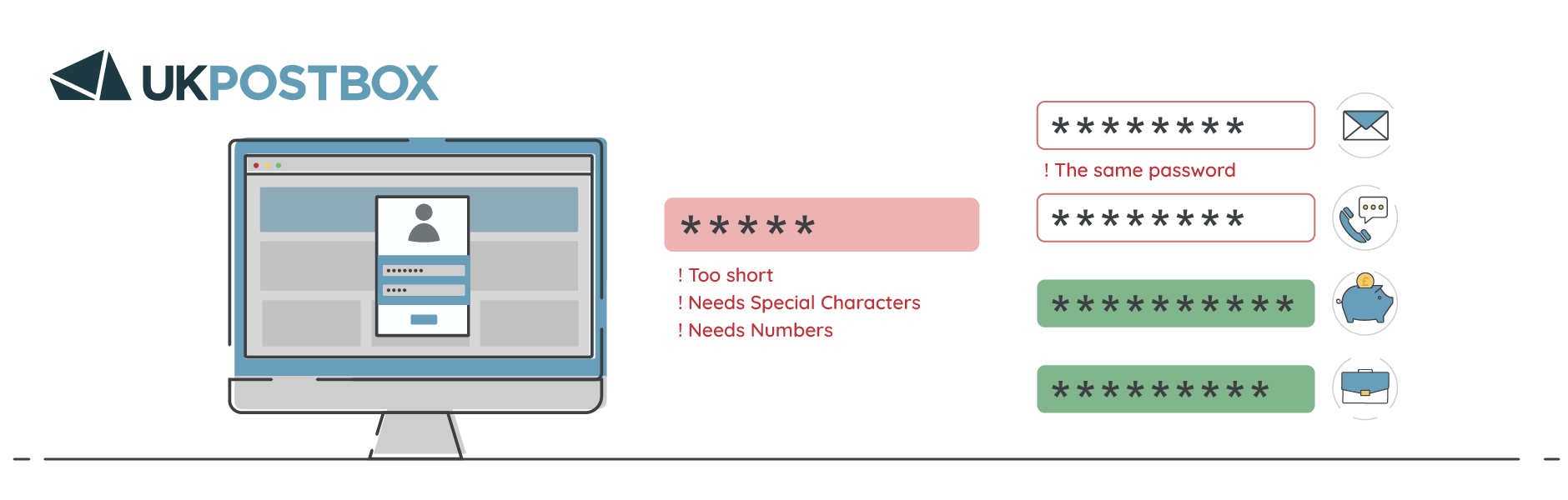
Tip 6: Create strong passwords using combinations, such as three random words
A strong password is your first line of defence against cyber criminals. It should be complex enough to be difficult to guess or crack, but also memorable so you don’t forget (unless you’re using a password manager). Using three random words together (Such as "MastDeckingSatellite") offers a strong base for your password before adding additional numbers and symbols. For example, the final password in this scenario could be MastDeckingSatellite867!?
Why it’s important
Weak passwords are one of the most common ways cyber criminals gain access to accounts. Simple passwords, such as "password123" or "qwerty," are easy to guess and can be cracked in seconds using automated tools. A strong password significantly reduces the risk of your account being compromised, making it harder for hackers to break in.
Tips for following this practice
- Use random words that don't relate to you personally: Avoid using words like your name, birthday, or any personal information that can be easily guessed or found online. Choose three unrelated words to make the password stronger.
- Add numbers and special characters: Enhance the security of your password by including numbers and symbols.
- Avoid using the same password for multiple accounts: Even if you have a strong password, using it across different accounts can still put you at risk. If one account is compromised, it can lead to others being hacked.
- Change passwords periodically: Regularly updating your passwords can help protect against long-term risks, especially if you suspect that your credentials may have been compromised.
Tip 7: Review the credibility of websites before sharing personal information
Before entering sensitive information such as passwords, credit card details, or personal data on a website, it's essential to ensure that the site is legitimate and secure. Cyber criminals often create fake websites that mimic reputable ones to trick users into revealing their information. Checking a website’s credibility can help you avoid these scams and protect your personal data.
Why it’s important
Scammers can set up fake websites that look nearly identical to real ones, hoping to trick users into entering their login details or payment information. Once they have this information, they can commit fraud, steal your identity, or gain unauthorised access to your accounts.
Tips for following this practice
- Check for HTTPS and a padlock icon: A secure website should have "https://" at the beginning of its URL, along with a padlock icon in the address bar. This indicates that the connection is encrypted. However, note that while HTTPS adds a layer of security, it doesn’t guarantee that a site is safe.
- Examine the website URL carefully: Scammers often use URLs that are very similar to the real ones, but with slight variations (e.g., "4pple.com" instead of "apple.com"). Make sure the URL is correct and doesn’t contain any unusual characters or misspellings.
- Look for clear contact information: Legitimate websites typically have clear and accessible contact details, including customer service numbers, email addresses, and physical addresses. If you can’t find this information, it might be a red flag.
- Read reviews and do a quick search: If you're unsure about a website, look it up online to see if other users have reported any issues. Reading reviews or checking forums can help you determine if the site is trustworthy.
Tip 8: Carefully review all emails before clicking on links or attachments
Emails are a common tool used by cyber criminals to launch phishing attacks, where they trick recipients into clicking on malicious links or opening harmful attachments. These emails often appear to come from trusted companies, but their goal is to steal your personal information, install malware, or redirect you to a fake website. Being vigilant about email content can help you avoid falling victim to such attacks.
Why it’s important
Phishing emails can lead to severe consequences, including identity theft, financial fraud, and device compromise. By clicking on a malicious link, you could unknowingly provide hackers with access to your accounts or allow malware to infect your device. Reviewing emails carefully helps you detect potential scams and keep your information secure.
Tips for following this practice
- Check the sender’s email address: Always examine the sender's address to ensure it's legitimate. Phishing emails often use addresses that look similar to official ones but have slight misspellings or extra characters (e.g., "support@paypa1.com" instead of "support@paypal.com").
- Look for spelling and grammar mistakes: Legitimate companies usually proofread their emails carefully, so emails with frequent errors can be a red flag. Phishing emails often have poor grammar, unusual phrasing, or misspelt words.
- Avoid clicking on unexpected links: Hover over links in emails to see where they lead. If the URL looks unfamiliar or doesn’t match the context of the email, do not click on it. Instead, go directly to the official website by typing the URL in your browser.
- Be cautious with attachments: Unless you are expecting an attachment, avoid opening it. Attachments can contain malware that will infect your device. If you are unsure, contact the sender directly using an official phone number or email address.
- Watch for urgent or threatening language: Phishing emails often try to create a sense of urgency, such as claiming that your account will be suspended unless you act immediately. Be cautious of emails that pressure you to take quick action.
Tip 9: Avoid posting your personal data publicly
Sharing personal information online can make you vulnerable to identity theft, phishing attacks, and other cyber threats. Information such as your email address, phone number, home address, and even seemingly harmless details (such as your pet's name or birthdate) can be used by cyber criminals to impersonate you or guess security answers. It’s essential to be cautious about what you share and where you share it.
Why it’s important
Cyber criminals often gather information from social media profiles, forums, and other online platforms to create targeted attacks. They can use your publicly shared data to craft convincing phishing scams, break into your accounts, or steal your identity. By limiting the amount of personal information you share, you make it harder for attackers to exploit your data.
Tips for following this practice
- Think before you post: Before sharing any personal information online, consider who can see it and how it might be used.
- Adjust privacy settings: Check the privacy settings on your social media accounts to control who can see your posts. Most platforms allow you to limit visibility to only friends or followers, reducing the risk of exposing your data to strangers.
- Be cautious with social media quizzes and games: Some social media games ask for information that could be used against you, like your birthdate or your favourite childhood pet. While they may seem fun, they can also be a tactic for gathering personal data. Avoid engaging in these quizzes if they ask for sensitive information.
- Use aliases where appropriate: When signing up for non-essential services or forums, consider using a username or alias that doesn’t reveal your real name or any other identifiable details This helps protect your identity, especially if the platform has weak security or is compromised.
Tip 10: Do not communicate with unknown individuals online
Engaging with people you don’t know online can open the door to various cyber risks, including scams, phishing attacks, and identity theft. Cyber criminals often pose as trustworthy individuals on social media, messaging platforms, or email to build trust and then exploit it. Being cautious about who you communicate with online can help protect your personal information and security.
Why it’s important
Many online scams begin with a seemingly innocent message from an unknown person. This could be a "friend" request on social media, a message in a chat app, or an email from someone claiming to need assistance. Once contact is established, scammers may try to extract personal details, financial information, or even manipulate you into taking actions that compromise your security. Avoiding contact with unknown individuals limits these opportunities for exploitation.
Tips for following this practice
- Ignore friend requests or messages from people you don’t know: Be cautious about accepting friend or follow requests on platforms like Facebook, Instagram, Whatsapp, Telegram and LinkedIn. Scammers often create fake profiles to connect with you and gather information.
- Avoid clicking on links sent by strangers: Even if a message seems harmless, clicking on links from unknown sources can lead to malicious websites or trigger malware downloads. If you receive a link from someone you don’t know, delete the message.
- Be wary of unsolicited offers or requests: Messages from strangers offering prizes, investment opportunities, or asking for help (e.g., money transfers) are often scams. Legitimate businesses or individuals are unlikely to reach out to you in this way without prior contact.
- Block and report suspicious accounts: Most platforms have options to block or report users who seem suspicious. If someone you don’t know is contacting you, especially if they are persistent or their messages seem unusual, report their account to the platform administrators.
Tip 11: Make your social media accounts private to limit exposure
Social media platforms are great for connecting with friends, family, and colleagues, but they can also expose your personal information to cyber criminals if your accounts are not properly secured. By setting your social accounts to private, you control who can see your posts, photos, and other sensitive details, helping to protect your privacy and security.
Why it’s important
Public social media accounts can reveal a lot about you, including your location, interests, habits, and even personal details like your birthday or family members' names. Cyber criminals can use this information to create targeted scams, guess passwords, or even steal your identity. Setting your accounts to private ensures that only approved followers can see your content, reducing the risk of misuse.
Tips for following this practice
- Adjust privacy settings on each platform: Review and update the privacy settings for all your social media accounts. Most platforms, including Facebook, Instagram, Twitter, and LinkedIn, allow you to limit who can see your posts, who can send you friend requests, and who can find your profile via search.
- Be selective with friend and follower requests: Only accept requests from people you know and trust. Even if you have mutual friends, consider whether you’re comfortable sharing your personal information with them.
- Limit the amount of personal information on your profile: Remove or hide sensitive information such as your phone number, address, and email address. This makes it harder for scammers to use your data against you.
- Regularly review your followers: Periodically check your list of followers or friends to ensure you still want them to have access to your posts. Remove or block any accounts that seem suspicious or that you no longer wish to share information with.
- Be cautious about tagging: Avoid tagging your location in real time, as this can reveal your whereabouts to strangers. Also, consider limiting who can tag you in photos and posts.
Tip 12: Avoid using the same password across multiple accounts
Using the same password for multiple accounts might seem convenient, but it’s a major security risk. If one of your accounts is compromised, it can give cyber criminals access to all other accounts that use the same password. Creating unique passwords for each account ensures that even if one password is exposed, your other accounts remain secure.
Why it’s important
When hackers obtain a password through a data breach, they often try it on various websites and services in a tactic known as "credential stuffing." If you’ve used the same password across multiple accounts, this could lead to a chain reaction of compromises, putting your email, banking, social media, and other important accounts at risk. By using unique passwords, you can limit the damage of a single breach.
Tips for following this practice
- Use a password manager: A password manager can generate and store complex, unique passwords for each of your accounts, eliminating the need to remember them all. You only need to remember the master password for the manager itself.
- Create passwords that are easy to remember but hard to guess: Consider using passphrases (a series of unrelated words) or a combination of letters, numbers, and symbols. Avoid simple patterns or common passwords like "123456" or "password123".
- Update weak or repeated passwords: If you discover that you have reused a password across different accounts, update it immediately. Start with your most important accounts, such as email and banking, and make your way down.
- Enable two-step verification (2SV): In addition to using different passwords, enable 2SV where possible. This adds an extra layer of security, making it harder for someone to gain access even if they have your password.
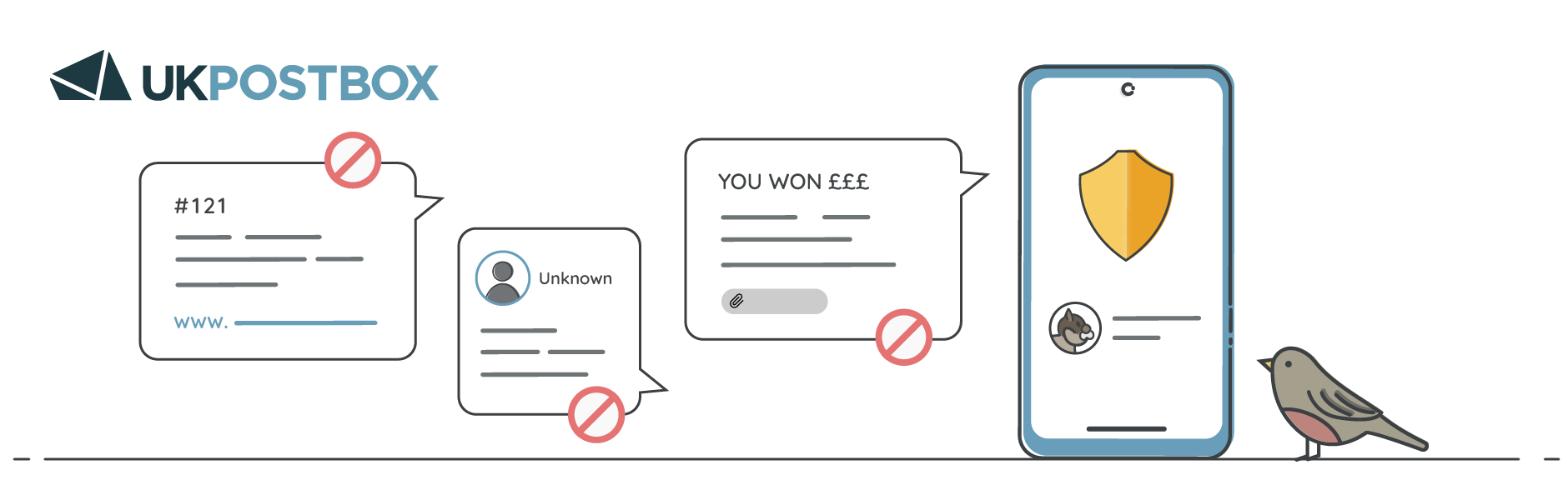
Tip 13: Do not click on links from SMS messages if you're unsure of the sender
SMS phishing, or "smishing," involves sending text messages that appear to be from legitimate organisations, asking you to click on a link or provide personal information. These messages often claim to be from banks, delivery services, or even government agencies, but the goal is to trick you into visiting a malicious site or downloading harmful software. Avoid clicking on links in SMS messages unless you are certain they are legitimate.
Why it’s important
Smishing can lead to serious consequences, including financial fraud, identity theft, and malware infections. Clicking on a malicious link can compromise your device, exposing sensitive information or causing it to become part of a larger botnet network. Being cautious about links in SMS messages helps protect your personal and financial data.
Tips for following this practice
- Do not respond to unexpected messages: If you receive an SMS from an unknown number or an organisation you don’t recall interacting with, do not respond. This could confirm to scammers that your number is active, leading to more attempts.
- Verify the sender independently: If the message claims to be from a known company (e.g., your bank or a delivery service), do not click the link. Instead, check the phone number or email address being used. Fraudsters will often mimic company names but use unrecognised contact details. If in doubt, contact the company directly through its official website or customer service number to verify the message.
- Watch for signs of phishing: Scammers often use urgent or alarming language to prompt immediate action, such as "Your account has been locked. Click here to resolve." Be wary of such messages, especially if they ask for personal information.
- Be cautious of shortened URLs: Shortened links (e.g., bit.ly, tinyurl) can obscure the actual destination, making it harder to tell if they are legitimate. Avoid clicking on shortened URLs sent via SMS unless you can verify the sender.
Tip 14: Do not respond to messages from unknown accounts
Receiving messages from unknown accounts on platforms such as email, social media, or messaging apps can be risky. Cyber criminals often use fake accounts to make contact, build trust, and then try to extract personal information or trick you into clicking on harmful links. It’s best to avoid engaging with unknown senders.
Why it’s important
Responding to messages from unknown accounts can lead to various cyber threats, including scams, identity theft, and malware infections. Engaging with suspicious messages can also signal to scammers that your account is active, increasing the likelihood of further attempts. By ignoring and reporting such messages, you reduce the risk of exposure to these threats.
Tips for following this practice
- Ignore and delete suspicious messages: If you receive a message from an account you don’t recognise, especially if it contains links or requests for personal information, don’t respond. Delete the message immediately.
- Be wary of messages with urgent or enticing content: Scammers often use tactics that make messages seem urgent (e.g., "You’ve won a prize!" or "Your account will be closed unless you act now"). Ignore these types of messages if they come from unknown accounts.
- Use platform tools to block and report: Social media and messaging platforms have tools that allow you to block and report suspicious accounts. If you receive a message that seems suspicious, report it to the platform administrators so they can take action.
- Check for signs of fake accounts: If someone you don’t know contacts you, check their profile for signs of a fake account, such as a lack of information, few followers, or recent account creation. Fake accounts are often used for scams.
Tip 15: Avoid saving your login details on shared or public devices
Saving your login details on shared or public devices might be convenient, but it poses a significant security risk. If someone else gains access to that device, they could easily log into your accounts without needing a password. Additionally, some public devices may have malware or keyloggers installed, which can capture your login information when you enter it.
Why it’s important
When you save your login details on a shared or public device, you risk compromising your accounts. This could lead to unauthorised access, data theft, or account misuse. Even if you trust the device, there’s no guarantee that others using it will not attempt to access your information. Avoiding this practice helps keep your accounts secure, especially in public places like libraries, internet cafes, or shared workspaces.
Tips for following this practice
- Always choose ‘Do not save’ when prompted: Most browsers will ask if you want to save your login details when you enter them. On shared or public devices, always decline this option.
- Use private browsing mode: When accessing your accounts on a public device, use private or incognito mode. This prevents the browser from saving your login information, browsing history, and cookies after you close the session.
- Log out after use: Always make sure to log out of your accounts when you’re finished, even if it’s your own device. This prevents others from accessing your accounts if they use the device after you.
- Clear browser data: If you have to use a shared device, clear the browser history, cookies, and cached data after logging out to ensure no trace of your session remains.
Tip 16: Be cautious of offers that seem ‘too good to be true’
Scammers often lure people in with offers that sound too good to resist, such as unbelievable discounts, free vacations, high hourly pay, or winning a lottery you never entered. These scams rely on the promise of something enticing to get you to click on a link, provide personal information, or even make a payment. Being cautious of such offers can help you avoid falling victim to these schemes.
Why it’s important
If an offer sounds too good to be true, it probably is. Scammers use fake promotions, giveaways, and special offers to trick people into providing sensitive information or clicking on malicious links. Falling for these scams can lead to identity theft, financial fraud, or malware infections. Learning to recognise these tactics can protect you from potential risks.
Tips for following this practice
- Question the legitimacy of the offer: Consider whether the offer makes sense. For example, legitimate companies don’t usually give away expensive products or large sums of money without a catch. If an offer appears out of nowhere, be cautious.
- Research the source: Check the website or sender to see if they are reputable. Look for reviews, complaints, or any information that might indicate whether the offer is real. Scammers often use names similar to well-known brands, but a quick online search can help verify their authenticity.
- Look for signs of a scam: Scams often use urgent language to make you act quickly ("limited time only," "act now"). If the message pressures you to click a link or share personal information immediately, take a step back and consider whether it’s genuine.
- Avoid providing sensitive information: If an offer asks for your personal or financial details in exchange for a prize, avoid sharing them. No legitimate giveaway will require your banking information upfront.
Tip 17: Never proceed with an action online if you're unsure of its safety
Sometimes, you may encounter a request or prompt online that seems suspicious or uncertain. Whether it’s an unexpected email asking you to click a link, a website requesting sensitive information, or a software download from an unfamiliar source, it’s essential to pause and evaluate the situation before proceeding. When in doubt, it’s better to err on the side of caution.
Why it’s important
Cyber criminals often rely on quick decisions and lack of awareness to trick people into taking actions that compromise their security. Phishing attacks, malware downloads, and other scams can occur when you proceed without thoroughly checking the safety of a request. By stopping to assess the situation, you can avoid falling into traps set by malicious actors.
Tips for following this practice
- Pause and evaluate the request: If you receive a request that feels off, take a moment to think it through. Consider whether it makes sense, if it’s expected, and whether you trust the source. Cyber criminals often use urgency to push people into making hasty decisions, so slowing down can help you spot scams.
- Verify directly with the source: If you receive an email or message from a company, and you're unsure if it's legitimate, contact the company directly using their official website or customer service number. Avoid using any contact information provided in the suspicious message.
- Check the URL before clicking: Hover over links to see the actual URL. If it looks unfamiliar or mismatched, don't click. It’s safer to go to the official website by typing the address directly into your browser.
- Consult with a trusted friend or expert: If you're uncertain, ask someone else for their opinion. Sometimes, a second set of eyes can confirm whether a request is legitimate or suspicious.
Tip 18: Install antivirus software and keep it updated
Antivirus software is designed to detect, block, and remove malware, viruses, and other harmful programs from your devices. Installing a reputable antivirus program and keeping it regularly updated ensures that your system is protected against the latest cyber threats. Even if you practise safe online habits, antivirus software acts as an additional layer of defence.
Why it’s important
Your device can be infected by malware by downloading a compromised file or clicking a malicious link. Without antivirus software, these threats can go undetected, potentially leading to data loss, identity theft, or even your device being used in larger attacks. Keeping antivirus software up to date ensures that it can identify new and evolving threats and protect your system accordingly.
Tips for following this practice
- Choose a reputable antivirus program: Opt for well-known and trusted antivirus software. Popular options include Norton, Bitdefender, Kaspersky, and McAfee. These programs offer comprehensive protection and are regularly updated to handle new threats.
- Set up regular scans: Schedule automatic scans at regular intervals, such as once a week, to ensure your system is checked for threats. You can also run manual scans if you suspect any suspicious activity on your device.
- Enable real-time protection: Most antivirus programs offer real-time scanning that monitors your device for potential threats as you browse the web, download files, or open attachments. Make sure this feature is enabled.
- Update antivirus software regularly: New types of malware are discovered all the time, so it’s essential that your antivirus software is up to date. Set it to update automatically to ensure you’re always protected against the latest threats.
Tip 19: Only download files from trusted, reputable sources
Downloading files from the internet can be risky if you’re not careful about where they come from. Cyber criminals often disguise malware as legitimate software, documents, or media files, tricking users into downloading and installing harmful programs. To avoid this, it’s essential to ensure that any file you download is from a trusted, reputable source.
Why it’s important
Malware can hide in various types of files, including software installers, PDFs, music files, and even images. Downloading from untrustworthy websites increases the risk of infecting your device with viruses, spyware, ransomware, or other types of malware. Once on your system, malware can steal personal information, damage your files, or allow hackers to take control of your device. Being cautious about what you download helps you avoid these threats.
Tips for following this practice
- Download software from official websites: Always get software directly from the developer’s official website or well-known platforms like Google Play, Apple App Store, or Microsoft Store. Avoid third-party sites that offer free versions of paid software, as they may include malicious modifications.
- Check for digital signatures: Some software providers use digital signatures to confirm that their files have not been tampered with. If you receive a warning about a missing or invalid digital signature when trying to install software, it’s safer to avoid it.
- Be cautious of file-sharing and torrent sites: These platforms can be breeding grounds for malware. Only use them if you trust the source, and even then, be cautious about what you choose to download.
- Scan files before opening: Use your antivirus software to scan downloaded files before opening them. Many antivirus programs offer real-time protection that can automatically scan files during download, but a manual scan can add an extra layer of safety.
Tip 20: Use a browser that offers enhanced security features
The web browser you use can significantly impact your online security. Some browsers come with built-in features that help protect against various cyber threats, such as phishing, tracking, and malware. Choosing a secure browser and enabling its safety features can add another layer of defence while you browse the internet.
Why it’s important
Browsers are often the gateway to many online activities, including accessing bank accounts, shopping, and managing personal data. Cyber criminals exploit browser vulnerabilities to carry out phishing attacks, install malware, or track users' activities without their consent. Using a browser with robust security features can help block these threats, keep your data private, and ensure a safer browsing experience.
Tips for following this practice
- Choose a browser known for security and privacy: Options like Google Chrome, Mozilla Firefox, Safari and Brave offer strong security features, including safe browsing modes, phishing and malware protection, and blocking of tracking cookies.
- Enable ‘Do Not Track’ requests: Most modern browsers allow you to send "Do Not Track" requests to websites, which can limit how much of your browsing data is collected.
- Use browser extensions to enhance security: Consider adding extensions like ad blockers, anti-tracking tools, and password managers. Popular extensions include uBlock Origin (ad blocking) and HTTPS Everywhere (forcing secure connections).
- Update your browser regularly: Browser developers frequently release updates to fix security vulnerabilities. Keeping your browser up to date ensures you have the latest protection against potential threats.
- Use private browsing or incognito mode when needed: If you’re accessing sensitive information, using private browsing can help prevent your data from being stored locally. This mode also prevents your browsing history from being saved.
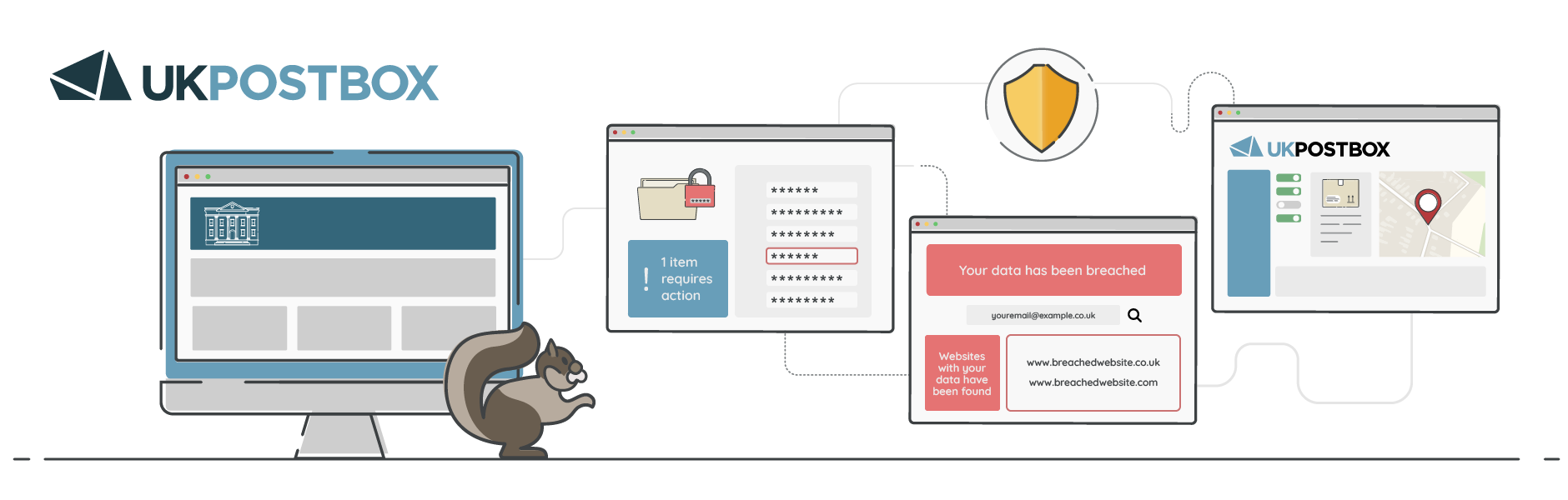
Tip 21: Check for common scams using online verification tools
Online scams are constantly evolving, and it can sometimes be difficult to tell if a message, website, or offer is legitimate. Fortunately, there are tools and resources available that help you verify whether something is a known scam. By using these tools, you can avoid falling victim to phishing attempts, fake offers, and other fraudulent activities.
Why it’s important
Scams can lead to financial loss, identity theft, and other serious issues. Cyber criminals often use tactics that make their scams look authentic, making it easy for unsuspecting users to be tricked. Using online verification tools can quickly alert you to known scams and prevent you from engaging with fraudulent websites, emails, or offers.
Tips for following this practice
- Use online scam databases: Websites like Action Fraud (UK), Scamwatch (Australia), and the Better Business Bureau (BBB) in the US maintain databases of reported scams. Check these sites if you receive a suspicious message or come across a questionable offer.
- Verify website safety with Google Safe Browsing: Google’s Safe Browsing tool lets you check whether a website is safe to visit. Simply paste the URL into the tool to see if it has been flagged for malicious activity.
- Check suspicious links with URL scanning tools: Tools like VirusTotal allow you to upload a file or paste in a URL to scan for potential threats. This can help you identify malicious websites before clicking on them.
- Search for reviews and complaints: If an offer or service seems questionable, search online for reviews or complaints. Often, other users who have encountered scams will share their experiences, helping you make an informed decision.
Tip 22: Periodically check if your data has been exposed in a data breach
Data breaches occur when hackers gain unauthorised access to a database, exposing sensitive information like usernames, passwords, and even financial details. It’s possible for your data to be compromised without your knowledge, which is why it’s important to periodically check if your information has been leaked in a breach. By staying informed, you can take quick action to secure your accounts and minimise potential damage.
Why it’s important
If your personal information has been exposed in a data breach, it could be used by cyber criminals for identity theft, phishing attacks, or unauthorised access to your accounts. Often, users aren’t aware that their data has been compromised until it’s too late. Regularly checking for breaches allows you to update your passwords, enable extra security measures, and monitor your accounts for suspicious activity.
Tips for following this practice
- Use breach-checking tools: Online services like Have I Been Pwned allow you to enter your email address and see if it has been involved in any known data breaches. If your information is found, take steps to change passwords and secure affected accounts.
- Enable alerts for future breaches: Some services, including password managers, can notify you if your data appears in a new breach. Enable these alerts to stay informed without needing to check manually.
- Change passwords immediately if exposed: If you find that your data has been compromised, change your passwords immediately. Make sure to use strong, unique passwords, and enable two-factor authentication (2FA) for additional security.
- Monitor accounts for suspicious activity: After discovering that your data was part of a breach, keep an eye on your financial and online accounts. Report any unauthorised transactions or access attempts to the appropriate authorities.
Tip 23: Use services to protect your personal information
Protecting your personal information often goes beyond just online safety practices. Services such as virtual addresses, virtual phone numbers, and secure mail forwarding can enhance your privacy by acting as intermediaries, ensuring that your personal details remain confidential.
Why it’s important
Your home address and phone number can be exploited by cyber criminals for identity theft, scams, and other malicious activities. Additionally, sharing these details online or using them for business can lead to unwanted contact or even physical security risks. Using services that mask or replace your personal information helps maintain your privacy and prevents unwanted exposure.
Tips for following this practice
- Use a virtual address for receiving mail: A virtual address service provides you with a secure, alternative address to receive mail. You can use this address for online shopping, business registrations, and other services without revealing your home address.
- Get a virtual phone number: A virtual phone number lets you make and receive calls without using your real number. This is particularly useful if you need to share your contact details for business purposes or online listings. Virtual numbers can be forwarded to your primary phone, allowing you to manage calls while keeping your main number private.
- Use a secure mail forwarding service: If you travel frequently or want to avoid sharing your address, a mail forwarding service can help. Your mail is sent to a secure address, processed, and then forwarded to your location or made accessible online. This ensures that your mail is handled discreetly and securely.
- Consider identity protection services: Some services offer comprehensive identity protection, which includes monitoring your personal information on the dark web, alerting you to potential security breaches, and helping you recover if your identity is compromised. These services add an extra layer of defence against identity theft.
Resources for staying safe online
Protecting yourself online is more important than ever, with cyber threats constantly evolving and our reliance on digital services increasing. By following the tips outlined in this guide, you can significantly reduce the risk of falling victim to scams, data breaches, and other online threats. From creating strong passwords to using specialised services, each step you take adds a layer of security that helps safeguard your digital life.
We’ve compiled a comprehensive list of resources to assist you in staying safe online:
- Password management: Use tools like LastPass, Bitwarden, Dashlane, and 1Password to create and store strong, unique passwords.
- Breach checking: Services like Have I Been Pwned and Firefox Monitor help you check if your data has been exposed in a breach.
- Password strength testing: Use tools like How Secure Is My Password to check the strength of your passwords.
- Phishing and scam detection: Action Fraud, VirusTotal, Google Safe Browsing, and PhishTank are great resources for verifying suspicious links, messages, and websites.
- Online privacy management: Use features like Google Chrome Incognito Mode and Microsoft Edge InPrivate Browsing for private browsing.
- Two-step verification (2SV/2FA): Use apps like Google Authenticator, Authy, and other authentication services to add an extra layer of security to your accounts.
- Email safety: Have I Been Pwned can alert you if your email has been compromised.
- Online file safety: Use tools like VirusTotal to scan files and URLs before opening or clicking on them.
- Cloud storage and data backup: Services like Google Drive and iCloud offer secure cloud storage solutions for backing up important data. Consider more comprehensive solutions like Acronis True Image for encrypted backups.
- Privacy services: Companies such as us offer virtual addresses and secure mail solutions to help keep your personal information private. Services like Google Voice provide virtual phone numbers to protect your contact details.
- Social media privacy settings: Use platform-specific guides to adjust privacy settings on popular social media platforms:some text
- Learn more about online safety from UK governmental services:
- National Cyber Security Centre (NCSC): Provides advice and resources on how to protect yourself and your business online, including their Cyber Aware campaign.
- Get Safe Online: A UK-based public and private sector partnership offering easy-to-understand advice on how to protect yourself, your devices, and your business.
- Action Fraud: The UK’s national reporting centre for fraud and cyber crime, where you can report scams and learn about common types of online fraud.
Consumer Protection Agencies: Useful for checking common scams and learning how to report them (Action Fraud in the UK).
Download our staying safe online checklist
Staying informed is the best way to navigate internet safety, and unfortunately, less tech-savvy individuals may be more prone than others. To help you share some of the information in this guide, we’ve created a simplified version you can download and share. Just use the link below for access.




